EB/EDISEC Xml and X509 Products
EB/EDISEC Presentation
EB/EDI*SEC offers high level security requests for signature and confidentiality for XML documents, HTML pages, data, and all document types.
EB/EDI*SEC is an easy to use library. Only few requests are needed to sign and encrypt or check secured objects.
EB/EDI*SEC can be used in environments needing strong security like e-business, document security, file transfers or e-banking.
The security envelop can be either XML/DSIG, XML/EDI5 , PKCS7,DSMS, ISIL or S/MIME.
EB/EDI*SEC utilizes the multi-providers security library EDI5X. Security devices: Etebac5, CryptoAPI, PKCS11or OpenSSL can be easily utilized including: smart cards, tokens, files or other.
EB/EDI*SEC offers Java, C interfaces applets for the Web.
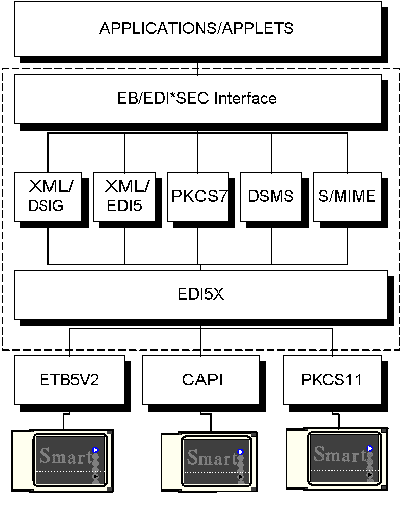
EB/EDISEC Specifications
The product offers C and Java interfaces as well applets (under Windows) for the Web.
PKCS7 and derivate formats Specifications:
- High level security requests for X509 signatures.
- PKCS7,DSMS & S/MIME envelops.
- Utilizes CryptoAPI and PKCS11.
- RSA-PKCS1 Signature on files, data & hash values.
- Simple and double signatures.
- SHA2, SHA384, SHA512, SHA1 & MD5 hashing.
- Detached and attached signatures.
- Signature including or not timestamping.
- Supports multiple devices simultaneously.
- Signed Files and data checking.
- Receipts generation.
- Receipts checking.
- Signed objects can be transmitted by any communication means.
- Suitable for e-business, corporate and banking projects.
XML/DSIG format Specifications:
- High level security requests for X509 signatures.
- XML/DSIG envelop.
- Utilizes CryptoAPI and PKCS11.
- SHAx-RSA-PKCS1 on files and data.
- SHA2, SHA384, SHA512, SHA1 & MD5 hashing.
- Minimal Canonical Transformation.
- Detached and attached signatures.
- Base64 Presentation.
- Supports multiple devices simultaneously.
- W3C/DSIG format proofs generation.
- Signed Files and data checking.
- Receipts generation.
- Receipts checking.
- Signed objects can be transmitted by any communication means.
- Suitable for e-business, corporate and banking projects.
Architectures
EB/EDI*SEC can be used in multiple types of architectures. Following are some examples of these architectures. These examples can be applied to e-business, electronic banking, EDI, ....
- File Transfer Architecture:
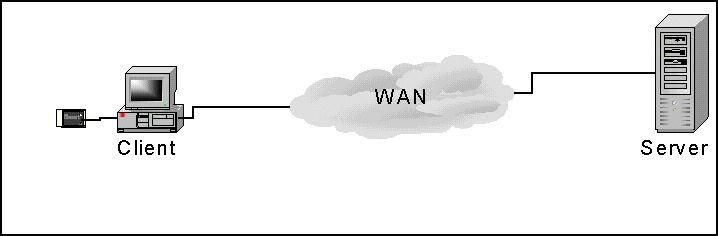
Le client prépare hors connexion ses données (Virements,Commandes, Déclarations, ...) . Une fois ces données saisies, formatées et validées le ou les signataires autorisés les signent. Les données sont transmises chez le partenaire par transfert de fichiers ou par messagerie. Les avantages sont bien sûr la préparation des données hors connexion, les informations sont locales chez le client; et le volume des données peut être relativement important. L'un des inconvénients de cette architecture est la mise à jour des logiciels du client.
EB/EDISEC peut être utilisé soit sous la forme de librairie ou de commandes batch côté client, serveur ainsi que sur les back-offices.
- Architecture full Web:
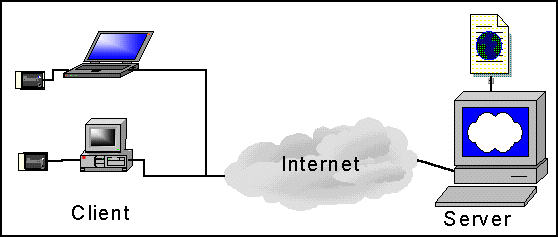
In this architecture the customer prepares his data in a connectionless mode(Payorders, Commands, Declarations, ...) . When data is prepared and validated it can be signed by authorised signers. The data is then tarnsmitted to the partner via File Transfer or a MHS.
The advantages of this architecture is the data preparing in the connectionless mode, all the information is local at the customer side and the huge volumes of information which can be treated and transmitted. One of the inconveniences is the update of software modules at the customer side.
In this architecture EB/EDISEC can be utilized as library or batch commands components at the customer side, server and the back-offices.
- Mixed Web/File Transfer Architecture:
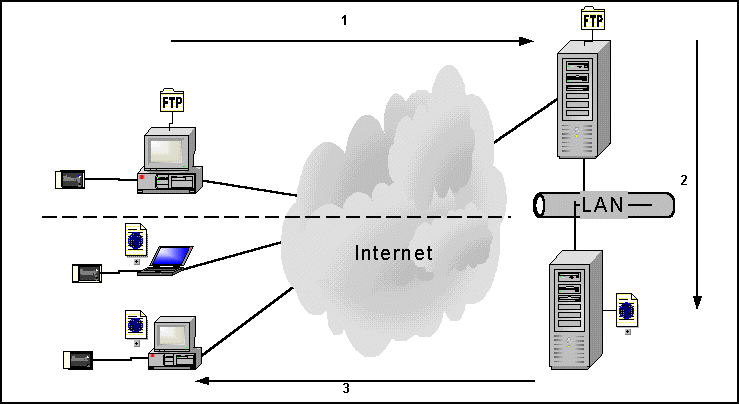
In this architecture the customer prepares its data in a connectionless mode (Payorders, Commands, Declarations, ...), then transfers the data to the partner server side by File Transfer or MHS(1).
The partner Web server picks the received data from the files server(2).
The customer can then connect to the Web server in order to validate and sign the transmitted information(3).
In this architecture EB/EDISEC is utilized as Java Applets at the customer side (Web Access). For files transfer, the partner server side and back-offices EB/EDISEC can be utilized as library or batch commands components.
- Alternative Mixed Web/File Transfer Architecture:
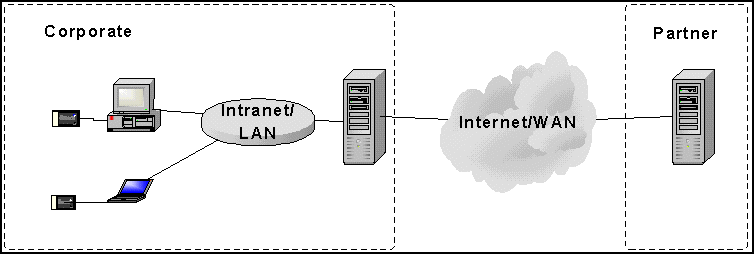
In this architecture the customer information is prepared, validated and signed via Intranet on the customer server.
The signed data can be then transmitted to the partner server by File Transfer or MHS.
In this architecture EB/EDISEC is utilized as Java Applets at the customer side (Web Access). For files transfer, the partner server side and back-offices EB/EDISEC can be utilized as library or batch commands components.